|
|
Britain rekrut pakar siber
[url=][/url]
Agensi khidmat pengintipan terbesar di Britain yang kini kehilangan pakar siber mereka kepada syarikat swasta yang membayar imbuhan lebih baik, semalam melancarkan satu pertandingan keselamatan dalam talian.
Pertandingan yang dibuka kepada semua warga negara Britain itu diperkenalkan bagi mengenal pasti dan merekrut pakar pengintipan masa depan negara itu. Selain aspek pengintipan, pertandingan itu juga turut berperanan untuk meningkatkan tahap kesedaran mengenai serangan siber.
Ibu Pejabat Komunikasi Kerajaan Britain (GCHQ) berkata, mereka yang berumur 16 tahun keatas dan masih belum bekerja dalam bahagian keselamatan siber, boleh memohon bagi menguji keupayaan mereka dalam perlindungan rangkaian komputer.
Namun, ia berkata, hanya 150 peserta yang disenarai pendek akan dibenar untuk bersaing.
Bimbang ancaman siber
Sementara ahli politik di seluruh dunia semakin bimbang dengan ancaman siber, Britain melihatnya sebagai perkara yang paling utama kerana GCHQ berdepan masalah mengekalkan pakar internet yang boleh meraih dua atau tiga kali ganda gaji mereka jika bekerja dalam sektor swasta.
Pengarah GCHQ, Iain Lobban yang memiliki kepakaran memecahkan kod dan memintas sistem komunikasi berkata pada Oktober tahun lalu bahawa kerajaan British dan sistem komputer industri menghadapi gangguan bilangan serangan siber yang menjadi ancaman kepada kesejahteraan ekonomi Britain.
Beri amaran
Ketua Pengarah Perkhidmatan Keselamatan MI5, Jonathan Evans dalam ucapannya pada Jun lalu, pula memberi amaran Britain bakal berdepan pengintipan siber dan kecurian berskala besar selain mengambil contoh kes sebuah syarikat senaraian awam di London kehilangan 800 juta (RM4 bilion) kerana kes serangan siber di negara itu.
Pertandingan dikenali sebagai Mengimbangi Sistem Pertahanan bermula pada 1 hingga 8 Oktober ini dan memerlukan pesertanya menganalisis replika rangkaian komunikasi sistem komputer kerajaan dan mencari kelemahan yang boleh dieksploitasi penggodam.
Penganjur berkata, peserta diminta mengenal pasti bentuk ancaman dan mencadangkan kawalan sistem pertahanan, khusus untuk aspek teknikal dan berasaskan dasar, bertujuan mengurangkan risiko di tengah peruntukan bajet yang ketat.
Ia berkata, peserta yang memohon mestilah warga negara Britain bermastautin di United Kingdom.
REUTERS
|
|
|
|
|
|
|
|
|
|
|
|
Spy chiefs spend £100m hiring cyber-war experts with some getting three times salary of GCHQ workers
Last year, MI5 spent £56.8 million on consultants - 73 per cent up on previous year
Bill predicted to rise 52 per cent to more than £80 million this year By Mail On Sunday Reporter
UPDATED: 00:42 GMT, 11 December 2011
Britain has spent more than £100 million in the past year on consultants to combat cyber espionage and the growing use of the internet by terrorists.
Now, MPs are investigating the soaring costs of employing private contractors, some paid the equivalent of £150,000 a year, three times the average wage at GCHQ, the Government’s signal and intelligence agency.
The specialists are mostly IT experts recruited to ensure the security agencies have state-of-the-art systems to run complex surveillance operations, thwart cyber attacks and provide digital back-up.

Soaring costs: MPs on the Intelligence and Security Committee are have appointed an independent investigator to review bills being paid by MI5, MI6 (pictured) and GCHQ
But MPs on the Intelligence and Security Committee are so concerned about the size of the consultancy fees, they have appointed an independent investigator to review bills being paid by MI5, MI6 and GCHQ.
Last year, MI5 spent £56.8 million on consultants, 73 per cent up on the previous year. This year, the bill is predicted to rise by 52 per cent to more than £80 million.
And GCHQ last year spent £43 million on 297 part-time contractors at its Cheltenham headquarters. Under last year’s spending review, all three agencies are facing an 11 per cent cut.
But the cutbacks have left gaps which are being plugged by outside contractors.
The huge fees paid are understood to have angered serving staff, some of whom are on salaries of less than £25,000.
Earlier this year, GCHQ directors complained they couldn’t keep staff because of poaching by Google and Microsoft which could afford to offer generous pay deals.
Whitehall sources argue that private consultant costs are high because of ‘public sector pay constraints’.
A GCHQ spokesman said: ‘GCHQ takes controlling the cost of consultants very seriously.’
|
|
|
|
|
|
|
|
|
|
|
|
 nak join cmner nak join cmner |
|
|
|
|
|
|
|
|
|
|
|
kakiputaralam posted on 21-9-2012 08:05 AM 
nak join cmner
Pertandingan yang dibuka kepada semua warga negara Britain |
|
|
|
|
|
|
|
|
|
|
|
GCHQ aims to recruit computer hackers with code-cracking websiteGovernment intelligence service targets 'self-taught' hackers with cryptic website that features no obvious branding
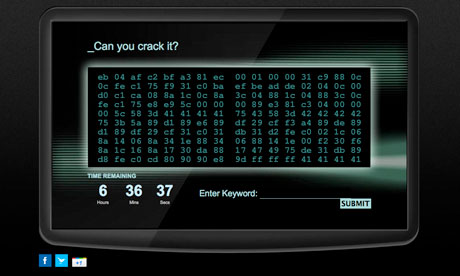
GCHQ's 'Can you crack it?' website ad
The government intelligence service, GCHQ, is aiming to attract the next generation of web-savvy spies by running an ad campaign that challenges computer hackers to crack a code to get an interview.
GCHQ, which reports to the foreign secretary and works with MI5 and MI6, has set up a website that is home to a tricky visual code.
The agency is drumming up interest in the code by seeding a message into social media, such as blogs and forums, that cyber specialists with a "keen interest in code breaking and ethical hacking" might frequent.
GCHQ usually hires its cyber specialists straight from college or university as graduates. However, the organisation admits that with the fast-moving world of computer technology it needs to tap the ranks of "self-taught" hackers as well.
The online marketing campaign, which has been developed by GCHQ's recruitment specialists TMP Worldwide, is being run without any branding for the agency.
GCHQ said, somewhat cryptically, that the campaign is anonymous "in order that applying for a career in the department is not the primary reason for the participant to engage".
"The digital arena is fast moving, and from a recruitment perspective we acknowledge the need to engage with prospective candidates in new and innovative ways," said a spokesman for GCHQ. "With this marketing initiative we hope to reach out to a broader audience, who may not be attracted to traditional advertising methods."
Somewhat ironically, given the campaign is aimed at computer hackers, GCHQ says that anyone who is found to have illegally hacked the code will not be eligible for recruitment.
GCHQ has employed unusual recruitment marketing tactics in the past.
In 2007 it ran an ad campaign in online games, including Tom Clancy's Splinter Cell Double Agent, to find those interested in a "career in British intelligence".
|
|
|
|
|
|
|
|
|
|
|
|
GCHQ's spy death riddle shines light on UK hacker war
Was Gareth Williams spotted at Blackhat or Defcon?
By Duncan Campbell Posted in Security, 3rd May 2012 11:14 GMT
British intelligence agent Dr Gareth Williams’ last mission before he was “unlawfully killed” was to infiltrate and report on US hacker meetings, evidence given at his inquest this week has indicated.
Williams appears to have been one of a team of intelligence officers and agents sent to penetrate hacking networks in the US and the UK.
At first sight he appears to be more Austin Powers than James Bond, but Williams is the first spy geek to be publicly unmasked, in sadly sensational circumstances.
His naked and decomposing body was found in the foetal position inside a sports holdall in the bath of his central London flat on 23 August 2010, one week after he had failed to turn up for work at SIS - aka MI6 - headquarters in Vauxhall Cross, London.
Coroner Dr Fiona Wilcox said yesterday that she was satisfied that a third party had placed the bag with his body into the bath and had also, “on a balance of probability”, padlocked it shut.
According to pathologists and escapologists who testified during her enquiry, the padlock on the almost airtight enclosure sealed his fate, stupefying and then killing him within minutes from CO2 poisoning.
His death was “was unnatural and criminally mediated”, she said. It was not suicide.

Gareth Williams
Who shut the lock on the holdall is a question that the coroner said could not be resolved with the evidence available. “Most of the fundamental questions in relation to how Gareth died remain unanswered," she said.
The compelling answer is a sex date a week before – somebody he had invited in to play bondage games and who may have panicked and fled when Williams lost consciousness, or sadistically locked the bag and left him to suffer.
Whoever he or she was, they did not leave enough DNA or forensic traces for detectives to have made progress to date. But the police forensic examination team, who checked through Williams' Mac laptop and iPhone collection, seem to have been blithely unaware of how many digital traces they may have missed or how much more may still be out there.
Williams’ last espionage targets were participants in the Black Hat and Defcon 18 hacker and security conferences held in Las Vegas in July 2010. His SIS manager told the enquiry that Williams was one of a “group” of agents tasked to attend the conferences.
The inquest was told about the unique Defcon 18 badge that had been found in his flat. The gimmick features a reflective display and an embedded digital signal controller that geeks were invited to manipulate.
Previously, as an operational officer, Williams had met two SIS agents working in the field in Britain, although not as their case officer or handler. Had he had not become cheesed off with SIS, the inquest was told, he would have been assigned abroad as a British secret agent. A few months before his death, he asked to go back to GCHQ.
Williams' working life, after graduating with a first in mathematics in 1996 aged 17, was spent in Cheltenham at GCHQ, Britain’s signals intelligence agency. He joined in 2001 after completing a PhD in computer science at Manchester University. His final role in GCHQ had been designing "practical applications for emerging technologies".
In 2007, he applied to become a secret agent by transferring to SIS, the UK's human intelligence agency responsible for spies and spy recruitment. He was put through a series of aptitude and skill tests. He failed. He also attended Black Hat 16 the same year, according to an SIS witness, presumably also then staying on to attend Defcon.
In 2008, he tried again to join SIS, and this time passed the tests. He started in spring 2009 after moving to London, and took part in five SIS training courses before embarking on "active operational work" within UK.
To spy on geeks, you need to hire a serious and thoroughly convincing geek.
|
|
|
|
|
|
|
|
|
|
|
|
GCHQ's spy death riddle shines light on UK hacker war
Was Gareth Williams spotted at Blackhat or Defcon?
By Duncan Campbell • Get more from this author
Posted in Security, 3rd May 2012 11:14 GMT
'There is a history of sending intelligence agents to Defcon'
Details of names he used and his “legend”, or cover story, for the Blackhat and Defcon conferences have not yet emerged. But government agents – certainly US government agents - trying secretly to take part are a familiar sight, according to regular conference participants.
There is a “history of sending intelligence agents to Defcon”, according to privacy researcher and former hacker Christopher Soghoian. The practice has become so familiar, it's now an established joke: event organisers pre-print stockpiles of prized T-shirts that announce “I spotted a Fed”.
Participants are invited to interrupt sessions to air their suspicions of a spy within the audience, much like parliamentarians making a point of order, according to Soghoian. The session chair must then invite the accused spook to confess. If they do, the accuser wins an “I’ve been spotted” T-shirt.
British spooks are not known to have being challenged or exposed in this way. But the quiet Welsh, lean, slim, short, fit young geek with cropped hair and a penchant for red T-shirts is unlikely to have passed unnoticed.
Save for exceptional tidiness, Williams’ London government-rented flat was equipped as a nerd should wish: two live Macs, parts of a dead Mac, four iPhones, loose SIMs, and assorted gear.
Digital clues found in Williams' flat
One of the iPhones, the inquest was told, was his “normal” phone, which GCHQ and SIS staff attempted to call when he failed to appear in his office. The others may have been used to cover identities. One of the iPhones, found in the lounge, had been operated on Sunday, 15 August, and reset to factory settings. At 23.54, that iPhone was backed up to his linked Mac Air laptop, potentially overwriting previously stored data and call or chat records. The Mac Air was used to browse the net for another 90 minutes, finally dropping in just after 1am on the web pages of the Evesham Wheelers, a cycling club near Cheltenham.
Hours later on Monday morning, he was probably dead, according to pathology reports on the degree of decomposition found.
Between July 2008 and August 2010, according to records found on the Apple tech, Williams had periodically browsed websites concerning fetish clothing and self-bondage, looked up “bondage training” on YouTube, and checked a wiki on hogties. He had artofcontstraint.com, an “adults only” website offering “exceptional bondage images”. The site has not been online since July 2011, but at the time Williams visited, it featured images and video of rope and bondage techniques. He had also made frequent visits to high fashion sites.
A loner with no identified sexual partners, he was said to have most enjoyed intense cycling, and fell running and climbing in Wales with his father. SIS’s internal culture had irritated him, causing him to break his secondment. He would have returned to GCHQ the month after his body was found.
Forensic phone examiner DC Robert Burrows, of SO15 Counter Terrorism Command, told the inquest that he had found no record of the identity of Gareth’s date on the likely fateful night. But he did find a homemade phone video in which the shy intelligence officer had stripped, put on boots, bent over a chair and waggled his rear at the camera.
Burrows and his colleagues who studied the Macs and iPhone appeared unfamiliar with Apple’s operating systems, and may not have realised what could be obtained by more sophisticated enquiries. He failed to mention iOS or any of its many features that could have revealed location-tracking geo-tags, address book contents and the phone's unique IMEI number - let alone any data passed to Apple and app makers.
The inquest forensically exposed wretched incompetence by the intelligence services as much as it threw a cruel spotlight on the intimate thoughts, leanings and experiments of a very private person. Williams’ SIS team leader testified under oath that he had called Williams on Tuesday, 17 August. But this claim was not supported by phone forensics or telephone company records. DC Burrows found instead that SIS had made a series of panic calls between 10am and 11am on Monday, 23 August. They were a week late.
Sir John Sawers, known as "C", has published an “unreserved” personal apology to the bereaved family.
Williams’ former co-workers at Cheltenham sit inside the largest data harvesting apparatus Britain has ever seen, an irony that should not be lost on the murder investigators that the Met will now deploy on more a detailed and complete enquiry.
GCHQ has led the demand for long-term storage of all communications records and social networking data, and for untrammelled access to internet providers' networks. They already exercise massive surveillance over the web. Will they tell the police that they cannot now trawl to find the telecommunications and contact data apparently erased the night before their own prize-winning officer died from his own exhalations?
And if not, perhaps they would like to drop in on Apple HQ and ask the geniuses there. ®
|
|
|
|
|
|
|
|
|
|
|
|
Asian hackers p0wned by Eastern European rivals
Former Soviet bloc countries hack hardest, says former presidential security man
By Phil Muncaster
Posted in Security, 20th September 2012 06:20 GMT
Cyber criminals from Eastern Europe present a more sophisticated information security threat to Western firms than their rivals in East Asia, according to a surprising new assessment of the global threat landscape by a former White House cyber security advisor.
Peter the Great vs. Sun Tzu is a new report from Tom Kellerman, cyber security VP at Trend Micro and until recently a commissioner sitting on The Commission on Cyber Security for the 44th Presidency.
In it, he reveals seven reasons why the researchers at Trend Micro believe “hackers from the former Soviet bloc are a more sophisticated and clandestine threat than their more well-known East Asian counterparts”.
Ever since the Operation Aurora attacks on Google and scores of other businesses came to light in 2010, targeted attacks or Advanced Persistent Threats (APTs) originating in China have accounted for the majority of high profile campaigns publicised in the media, including Night Dragon, Ixeshe and Luckycat.
However, Eastern European cyber criminals tend to use more sophisticated, customised malware, built without third party tools and often featuring “robust anti-debugging techniques and complex command-and-control”, according to Kellerman.
Eastern European attacks are a legacy of high quality science and maths education in Soviet bloc countries. Kellerman says the highly competitive nature of the Eastern European underground also helps to produce malware “ so elegantly crafted as to be the 'Faberge Eggs' of the malware world."
Infrastructure including DNS servers also tends to be developed in-house, with the cyber hoodlums aiming to maintain control of the entire stack.
East Asian operators, by contrast, use cheap, hosted infrastructure as they’re less bothered about being identified. They also tend to employ simpler, off-the-shelf malware to get the job done.
Eastern European hackers are organised in small, independent mercenary units which live or die by the quality of their work and are motivated solely by profit, meaning they’re capable of more precise and focused attacks and aim to steal credentials that can be sold on the black market.
The report likens East Asian cyber criminals, on the other hand, to “cyber foot soldiers” tasked with gathering information for their commanders – more focused on longer term strategies and better insulated from any losses or failures.
Given that reputation and profit is everything, hackers from the former Soviet bloc go to great lengths to stay hidden, whereas their East Asian rivals, once inside the network concentrate on “lateral movement, use of command-line tools, and passing of credentials”, the report said.
“The thousand grains of sands approach is symbolic of an East Asian colonisation as the reconnaissance is ongoing and the battlefield not necessary prepped like the East European model,” wrote Kellerman. ®
|
|
|
|
|
|
|
|
|
|
|
|
Hidden Dragon: The Chinese cyber menace
'Any decent government does industrial espionage'
By John Leyden
Posted in Security, 24th December 2011 10:00 GMT
Analysis Cybercrooks and patriotic state-backed hackers in China are collaborating to create an even more potent security threat, according to researchers.
Profit-motivated crooks are trading compromised access to foreign governments' computers, which they are unable to monitise, for exploits with state-sponsored hackers. This trade is facilitated by information broker middlemen, according to Moustafa Mahmoud, president of The Middle East Tiger Team.
Mahmoud has made an extensive study of the Chinese digital underground that partially draws on material not available to the general public, such as books published by the US Army's Foreign Military Studies Office, to compile a history of hacking in China. His work goes a long way to explain the threat of cyber-espionage from China that has bubbled up towards the top of the political agenda over recent months.
The first Chinese hacking group was founded in 1997 but disbanded in 2000 after a financial row between some of its principal players led to a lawsuit. At its peak the organisation had about 3,000 members, according to Mahmoud. The motives of this so-called Red Hacker group were patriotic, defending motherland China against its enemies.
The hacking the US Embassy and the White House over the accidental bombing of the Chinese Embassy in Belgrade back in 1999 brought many flag-waving Chinese hackers together to, as they saw it, defend the honour of the motherland and fight imperialism in cyberspace.
This role was taken over by the Honker Union of China (HUC) after 2000, and the HUC later became the mainstay of the Red Hacker Alliance. China’s so-called “red hackers” attack critics of the state and infiltrate foreign government and corporate sites – among other activities. The phenomenon of patriotic hackers is far from restricted to China and also exists in Russia, for example. Russian hackers tend to make greater use of defacement and botnets to silence critics rather than spying.
Enter the Dragon
Over more recent years, different groups – which are involved in cybercrime to make money rather than patriotic hacking – have emerged in China, some of which are affiliated with the Triads. These groups are involved in running so-called bulletproof hosting operations, providing services for other phishing fraudsters and the like that ignore takedown notices that ethical ISPs would comply with - as well as various botnet-powered scams, spam and paid-for DDoS attacks for hire. "These firms did not target Chinese firms and were are therefore not prosecuted," Mahmoud explained.
Over the years patriotic hacker groups and criminal hackers have forged alliances, a process facilitated by the Chinese government and in particular the Peoples' Liberation Army, according to Mahmoud. One landmark event in this process was the defacement of Western targets and similar cyber-attacks following the downing of a Chinese jet by US warplanes in 2001. These attacks promptly ceased after they were denounced by the People's Daily, the organ of the ruling Communist Party.
The Chinese government began to see the potential of cyberspace at around this time and established a PLA hacking corp, as Mahmoud described it, featuring hand-picked soldiers who showed talent for cyber-security.
Mahmoud said that despite the existence of this corps the Chinese often prefer to use "freelance hackers" for "plausible deniability". "We can talk about hackers but it's better to talk about businessmen selling secrets. An entire underground industry has grown up to support cybercrime," he said.
There are various roles within such group including malware distribution, bot master, account brokers and "most importantly vulnerability researchers, whose collective ingenuity has been applied to run attacks against Western targets and to develop proprietary next-generation hacking tools", according to Mahmoud.
Small groups, including the Network Crack Program Hacker (NCPH), that research gaping security holes and develop sophisticated malware strains are reportedly sponsored by the PLA.
Western governments, hi-tech firms, oil exploration outfits and military targets have variously been targeted in a expanding series of so-called Advanced Persistent Threat (APT) cyber-attacks, commonly featuring Trojan backdoors, over the years. These operations have been known as TitanRain, ShadyRAT and Night Dragon, among others.
"It's sometimes difficult to differentiate between state-sponsored and industrial espionage attacks but what's striking is that all these attacks happen between 9am and 5pm Chinese time," Mahmoud noted.
Gaining access to industrial secrets is part of a deliberate targeted government plan, Programme 863, whose mission aim is to make Chinese industry financially independent of foreign technology. It also has a military dimension. "China sees cyberspace as a way of compensating for its deficiency in conventional warfare, for example by developing strategies to cripple communication networks," Mahmoud said. "That does not mean China wants to fight. Inspired by the ideas of Sun Tzu [author of The Art of warfare] China regards it as a superior strategy to break the enemy without having to fight."
North Korea is also developing expertise in cyber-warfare, running training schools that resemble those run in China. However there is little or no collaboration between the two countries, according to Mahmoud.
"The Chinese see their expertise in cyberspace as an edge they are not willing to share. That's why there is no collaboration with hackers outside the country."
The Wall Street Journal reported last Tuesday that US authorities have managed to trace several high-profile hacking attacks, including assaults against RSA Security and defence contractor Lockheed Martin, back to China. Information obtained during an attack on systems behind RSA's SecurID tokens was later used in a failed attack against Lockheed Martin.
"US intelligence officials can identify different groups based on a variety of indicators," the WSJ reports. "Those characteristics include the type of cyberattack software they use, different internet addresses they employ when stealing data, and how attacks are carried out against different targets. In addition to US government agencies, major targets of these groups include US defence contractors."
US investigators working for the National Security Agency have reportedly identified twenty groups of hackers, a dozen of which have links to China's People's Liberation Army. Others are affiliated to Chinese universities. In total, several hundred people are said to be involved in the attacks, some of whom have been individually identified. The information has helped to strengthen the US's hand in diplomatic negotiations with China.
The data also provides a list of targets for possible counter-attacks.
Bloomberg reports in a similar vein that China is engaged in an undeclared cyber Cold War against Western targets with the goal (unlike the Soviet-era Cold War) of stealing intellectual property rather than destabilising regimes or fostering communism.
Targets have included tech giants such as Google and Intel to iBahn, selected because it supplies Wi-Fi technology to hotels frequented by Western execs, oil exploration biz bosses and government and defence contractors. Chinese hackers stand accused of stealing anything and everything that isn't nailed down from as many as 760 different corporations over recent years resulting losses in intellectual property valued in the billions.
|
|
|
|
|
|
|
|
|
|
|
|
|
james bomb junior mesti kena pandai komputer |
|
|
|
|
|
|
|
|
|
| |
|